| □ | Below is a list of special Second Edition UL® 1981 Standard definitions and specific installation and operational requirements, along with a diagram of a Second Edition UL® 1981 Standard Configuration - many of which may be referenced elsewhere in this manual. |
| • | Active System - (reference Item 3.2 Second Edition UL® 1981 Standard) |
| • | Any system that is preprogrammed to send more than 1 signal per day to the central station automation system is, by definition, an Active System. |
| • | SPD - Surge Protection Devices - (reference item 4.3.(e) Second Edition UL® 1981 Standard) |
| • | The automation system hardware primary power source shall be protected by surge protective devices (SPD) that comply with the Standard for Surge Protective Devices, UL 1449. |
| • | The SPD shall have a Maximum Continuous Operating Voltage (MCOV) equal to or greater than the normal operating voltage of the system. |
| • | The SPD Type Designation (Type 1.2. or 3) must be suitable for the installation application. |
| • | Signal-line transient protection - (reference item 4.3.(f) Second Edition UL® 1981 Standard) |
| 1. | The communication circuits contained within the central-station building and not connected to the telecommunications network shall be protected by isolated loop circuit protectors. These protectors shall comply with the Standard for Protectors for Data Communications and Fire Alarm Circuits, UL 497B, and shall have a marked rating of 50 volts or less. |
| 2. | Communication circuits connected to the telecommunications network shall be protected by secondary protectors for communication circuits. |
| • | These protectors shall comply with the Standard for Secondary Protectors for Communications Circuits, UL 497A, and shall have a marked rating of 150 volts or less. |
| • | These protectors shall be used only in the protected side of the telecommunications network. |
| • | Exception: Equipment connected to telecommunications circuits which has been evaluated to the requirements of the Standard for Control Units for Fire-Protective Signaling Systems, UL 864, are not required to have protection devices evaluated to the requirements of UL 497A. |
| • | The receivers are located in the same room or area as the operators - (reference item 13.2(c) Second Edition UL® 1981 Standard) |
| • | A partition made of glass or other durable, transparent material may separate the operators from the receivers. |
| • | This partition shall not prevent operator access to the receivers. |
| • | All the network equipment through which signals pass is redundant - (reference Item 13.2(f) Second Edition UL® 1981 Standard) |
| • | All the network equipment through which signals pass is redundant. |
| • | Redundancy is capable of being achieved by having back-up network equipment placed near the on-line unit so that connection to the network is accomplished in 6 minutes. |
| □ | UL® Listed System Installation & Configuration Diagram - (reference Item 15.5 Second Edition UL® 1981 Standard) |
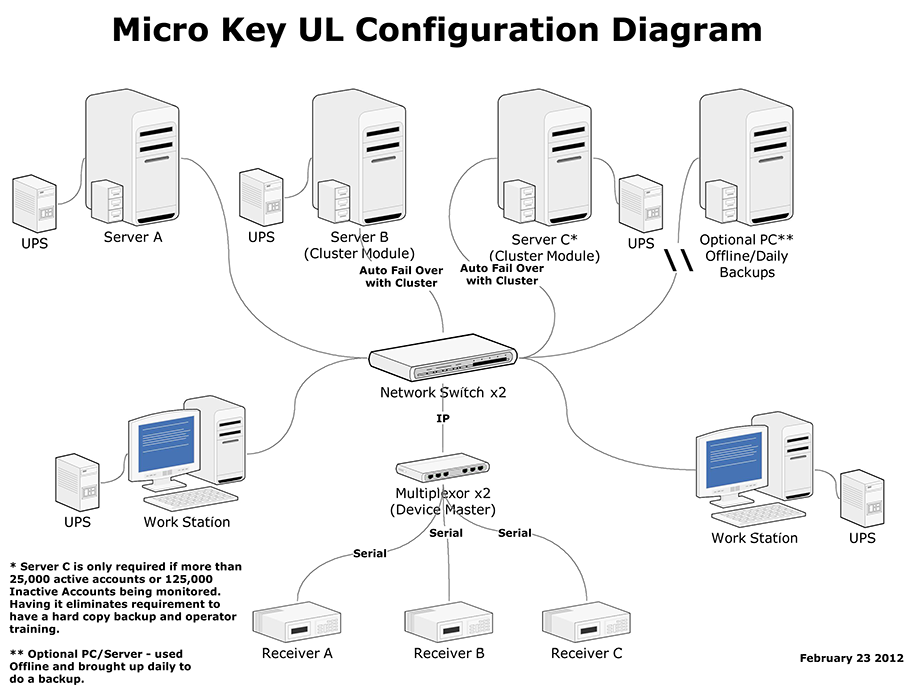
| • | Backup Computers - (reference Item 13.5(e) Second Edition UL® 1981 Standard) |
| • | The second back-up computer shall have its own UPS which meets all of the requirements specified in this standard or is configured in such a way that it is capable of being connected to the primary or first back-up computer’s UPS in time to meet the requirements of 13.5(b). |
| • | Backup Database - (reference Item 13.5(d) Second Edition UL® 1981 Standard) |
| • | The alarm system data base on the second back-up computer shall be updated not less than once every 24 hours. |
| • | All the network equipment through which signals pass is redundant. - (reference Items Item 13.2(f) and 13.5(e) Second Edition UL® 1981 Standard) |
| • | Redundancy is capable of being achieved by having a back-up network equipment placed near the on-line unit so that connection to the network is accomplished in 6 minutes. |
| • | Manual Records storage - (reference Item 16.3 Second Edition UL® 1981 Standard) |
| • | Manual records (paper records, microfiche, personal computer storage) shall be kept in the operating area for reference in the event of loss of the automation system. These records shall be updated biweekly. |
| • | Exception: Central-Stations that use a second back-up computer meeting the requirements of 13.5 are not required to comply with the requirement of 16.3. |
| • | Records Availability - (reference Item 21.2(a) Second Edition UL® 1981 Standard) |
| • | The most recent record of the alarm system data base shall be maintained and be readily available for all Accounts. This record shall include, as appropriate, dispatch instructions, disarming and arming (opening and closing) schedules, pass card data, holidays observed and schedules , and the time and date that the data file was created. Additionally, record data shall meet the requirements specified in the Records sections (fire alarm, and burglar alarm) in the Standard for Central-Station Alarm Services, UL 827, as appropriate. |
| • | Security Access - (reference Item 24.3 Second Edition UL® 1981 Standard) - The automation system shall have a minimum of four levels (or degrees) of security. |
| • | In order to operate the automation system, a security sign-on code consisting of not less than six alpha numeric characters shall be required. |
| • | The security sign-on shall govern the access level. |
| • | The levels of security shall be as follows: |
| a) | Minimum security level (i.e., Trainee) – Shall permit acknowledgment of operator actions in response to signals received from alarm systems. |
| ▪ | It shall also permit printing or electronic copying of alarm system records. |
| ▪ | This level shall not affect the ability of the automation system to perform its alarm system monitoring functions. |
| b) | Second security level (i.e., Operator) – Shall permit temporary (24 hours maximum) suspension of the automation system’s designated activity for specific functions of an alarm system. |
| ▪ | The preprogrammed condition shall automatically be restored within a predetermined time of change of function. |
| ▪ | Suspension may be repeated at the discretion of the central-station staff with this security level. |
| c) | Third security level (i.e., Supervisor) – Shall permit permanent record changes to the automation system’s alarm system data base such as adding, deleting, or suspending Accounts for longer than 24 hours. |
| d) | Fourth security level ( (i.e., Manager/Administrator) – Shall provide the ability to change central-station operator IDs, or changes to time and date. |
| ▪ | The user shall not be able to change the time and/or date of change-of-status signals that are received and processed, including dispatch, arrival, and similar information. |
| e) | High security level ( (i.e., Micro Key Development Staff Only) – Shall provide capability for permanent modification of the alarm monitoring software. |
| ▪ | This is intended to be a level only accessible to the software provider’s programmers. |
| • | Upon resolution of a fire, hold-up, or burglar alarm incident, the automation system shall automatically generate an alarm report for certificated Accounts and record it on non-volatile memory. |
| • | The system shall be capable of generating an alarm report upon demand for non-certificated alarm systems. |
| • | This report shall include the following items, as applicable: |
| a) | The name and address of the subscriber (fire/burglar); |
| b) | The type of alarm (burglary, hold-up, fire); |
| c) | The designated response time (burglar); |
| d) | Whether there is standard or encrypted line security. When provided, it shall be indicated; |
| e) | The time the alarm was received by the automation system (fire/burglar); |
| f) | The time the police / fire department was notified, and the police / fire department identification number (fire/burglar); |
| g) | The time the alarm investigator No. 1 was dispatched, and the investigator's name and employee ID (burglar); |
| h) | The time the alarm investigator No. 2 (if any) was dispatched, and the investigator's name and employee ID (burglar); |
| i) | The time the alarm investigator No. 1 arrived (fire / burglar); |
| j) | The time the alarm investigator No.2 arrived (if dispatched) (fire / burglar); |
| k) | The elapsed time between the receipt of the alarm signal at the central-station automation system and the investigator's arrival at the protected premises; |
| l) | The method used to verify the alarm investigator's arrival such as radio, telephone, or other means (fire / burglar); |
| m) | Whether the central-station holds keys; |
| n) | Whether the keys were used or not used (fire / burglar); |
| o) | The time the subscriber was notified, the name of the notified subscriber (2 or 3 lines might be required for multiple notifications) (burglar / fire); |
| p) | The disposition of the alarm (fire / burglar); and |
| q) | Whether a sounding device is provided on the alarm system (optional). |
| ► | Note:See the UL® Signal Processing Procedures chapter for more information relating to these 20.8(a-q) in the Second Edition UL® 1981 Standard items. |
| □ | The Virtual Printer application provides a phantom printer connection to store Receiver Printer Output in a computer file. |
| • | The Virtual Printer application was designed to help Central Stations reduce the amount of paper it uses over the course of time. |
| • | Signal traffic from Accounts out in the field is very important and is usually preserved by having the information printed as it comes in from the receiving equipment. |
| • | This recording process can cost the central station hundreds of dollars in paper and ink costs each month. |
| • | The Virtual Printer application allows the signal traffic that would normally be printed out on plain paper, to be captured and saved to a computer database and stored on a hard drive. |
| • | The Virtual Printer application also allows the end user to review any data received by the receiver for any time period and print it out if so desired. |
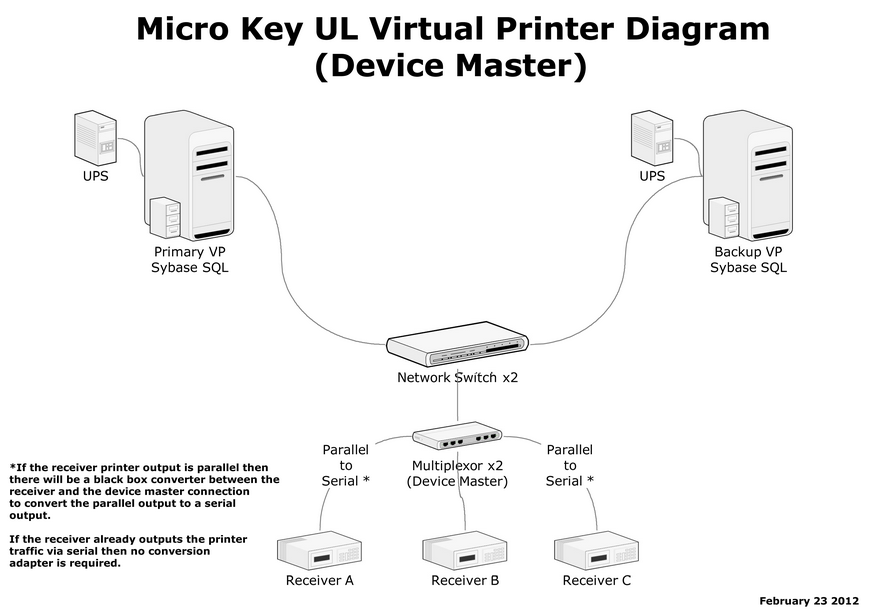
Micro Key UL$ Virtual Printer Diagram installation utilizing a Device Master





